What You Should Know About IoT Security
Of Issues protection in the event of Web, it is the Wild West available. Drones with guns connected, vehicles that are, linked slightly sabotaged — the possibility of difficulty appears to be limitless. Actually well known, culture has been engaging in the work. Witness Valley occurrence where in actuality the home- its location suddenly changes and enters a shipping-container, getting Jared to some man made isle in the Ocean’s middle (sorry, what? Friend vehicle? Pardon me?”).
The internet danger situations develop tremendously once we look at a potential globe with more than 25 million linked “things” being used by 2020. In a post – that was preceding – Iota fulfills with the Web of Actions. I defined some of the options — a number of that have currently materialized recently. Linked house compromised to start the leading doorway to robbers. Available garage-door to grab an automobile, increase heater to optimum amounts to harm AC system and/or home products, turn fully off fridge, turn fully off sprinkler program, entry PCS, and etc.
Independent that is linked vehicle or shipping automobile delivered to wrong locations, or sabotaged to accident via braking or improper speed; automobiles boats, such as for instance trains drones etc. sabotaged or likewise misdirected. Linked clinic compromised to alter the path of shipping spiders. Capabilities of medical devices such as for instance pumps and pacemakers, a such like.
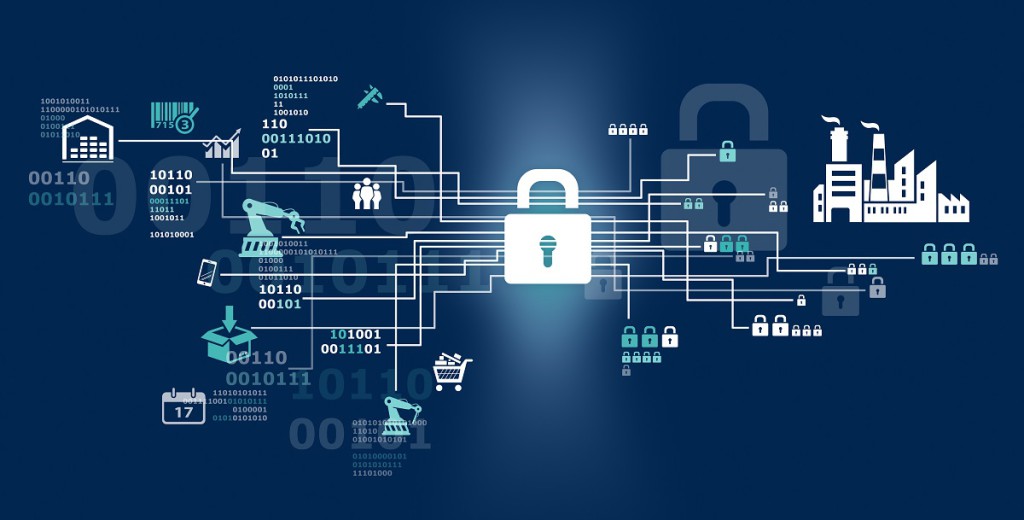
Linked producer compromised to disrupt capabilities of supply-chain actions, gear checking and upkeep devices, place control-systems, factory “picking” spiders, such like. SCADA methods sabotaged towards the worm that span nuclear centrifuges in comparable style. The ensuing “damage” may vary from annoyance problems completely too severe problems associated with harm to bodily home or lack of existence, possible damage, and on occasion even risks to national-security.
Recruiting in complete safety: why is protection so hard?
Among the primary issues, compounding this case is that protection is usually an afterthought, bolted following the reality onto options, once problems occur. IT security specialists also it supervisors have already been phoning for protection to become integral by-design for many years today, but there’s been an extended type of engineering improvements which range from the Net, to flexibility and cloud-computing, and now towards the Iota, where it nevertheless feels as though, and frequently is, an afterthought.
Additional problems are, created by incorporating protection following the reality as well. They produce setbacks in recognizing their complete company advantages as businesses find it difficult to apply suitable protection settings while rising systems are not safe from the beginning. Actually, research on Obligation and “Risk in a from the Globe Economic Community projected setbacks handling internet danger ranged to a few months for interpersonal processing, to 5 weeks for Iota and flexibility, from 11 weeks for cloud. Obviously, a bigger proportion of IT security that is usually smooth invest must be redirected here versus border protection.
What contributes to this trouble, of acquiring the Iota in the event, is the fact. That it is an environment – that is complex. Iota options and providers are usually made up of not only one-product, but a program of methods which includes equipment and application from a variety of suppliers, similar to RFID methods within the early-2000s, where you’d to cope with a number of labels, visitors and middleware — all from various events.
The protection of the entire answer is just like its lowest link, which means extra weaknesses for cybercriminals open up and makes finish-to-end screening important. A few of the primary weaknesses are, investigated of Issues Top Task in the Wild Website Software Security (OWASP) Web.
Preventing the gunfight: A construction to consider danger
While considering risk amounts associated with Iota protection, it is helpful to understand where in actuality the main problems might occur once hackers reach their goal location via the internet “kill chain.” one method to consider this would be to think about the numerous types of Iota products and also the related kinds of internet danger. As products become even more independent or more manageable, the risk strength increases as cyber criminals can grab sensitive information, expose spyware, and fundamentally conduct – sabotage.
Among the frameworks I have discovered helpful has been Gartner’s category of four types of Iota products, which range from recognizable issues (e.g., passive RFID labels), to speaking/feeling issues (e.g., stress receptors), to manageable feeling issues (e.g. HVAC programs), to wise independent issues (e.g., home-driving vehicles). This category is, shown by the number. Having a tough feeling of internet danger highlighted along side’s kinds.